Is the Phone Scam Episode in Taxi Driver 3 Actually Possible in Real Life?
Recurring Scam Structures in Second-hand Trading and Random Chat. Alternatives via diptok

Hello, I'm Ji-Hoon Kim, sharing data-driven insights. Today, I want to analyze the phone and second-hand trading scam episode from the recent hit K-series Taxi Driver 3.
Following the broadcast, some viewers reacted by saying it was a "setup only possible in a series." However, looking at the structural elements, this episode is not much different from the patterns of phone scams, second-hand trade scams, and online scams that are already occurring repeatedly in reality. A similar example is the 2023 movie Unlocked, which was a fictionalized adaptation of actual incidents involving smartphone security breaches.
In this post, I want to focus on why the phone scam episode in Taxi Driver 3 is realistically possible and what structural problems it reveals.
The Core Structure of the Taxi Driver 3 Phone Scam
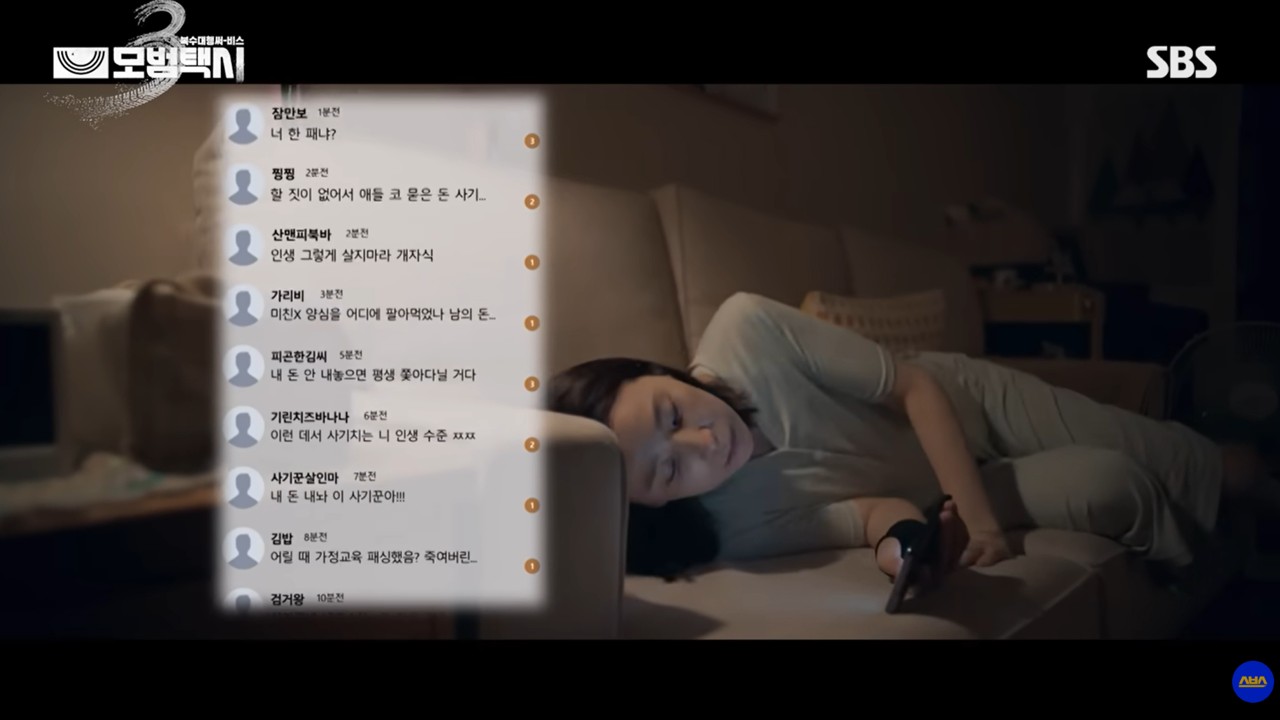
The phone scam depicted in Taxi Driver 3 does not stop at mere financial loss. Contact initiated through a second-hand trade leads to the exposure of a phone number. Subsequently, the victim is manipulated into being misunderstood as the perpetrator, leading to the collapse of their daily life.
This flow is very similar to the increasing number of second-hand trade and online scam cases today. Even if the initial financial loss is small, secondary damage often occurs through personal information naturally exposed during the transaction process, and the scope of that damage expands rapidly.
From Second-hand Trading to Phone Scams

Many phone scams occurring in reality start with second-hand trade scams. Approaching victims with bait—such as high-demand concert tickets, electronics, or smartphones—inducing them to move to external messengers, and avoiding secure payment systems are methods that have been used repeatedly.
At this stage, many victims believe the problem is over once the "transaction" is finished. However, in reality, this is the point where phone numbers and account information are handed over to the scammer, often leading to additional crimes mediated by the phone.
The most realistic part of the Taxi Driver 3 episode is the misuse of the phone number that begins after the initial scam. The scammers do not always use technical means like hacking. They use the already obtained phone number to directly disrupt the victim's life. This includes making false orders on delivery apps, posting fake giveaways of expensive items on second-hand sites, sending spam messages, and exposing the number on online communities. The victim is forced into a constant state of having to explain themselves. As a result, the victim is easily perceived not as the person who was scammed, but as the person causing the trouble.
Escalation into Psychological Dominance
The episode in Taxi Driver 3 goes one step further. The scammer induces the victim to remain constantly conscious of them. By sending messages that imply they know the victim's location or sending photos of the victim's daily life, the scammer suggests continuous surveillance and applies psychological pressure.
From this stage, the crime can be viewed as a complex hybrid of phone scamming, cyberstalking, and blackmail. Actual legal precedents show that these types of crimes take much longer to recover from compared to simple fraud.
Why Do These Phone and Online Scams Repeat?
The reason the Taxi Driver 3 phone scam episode feels realistic lies more in the vulnerability of the conversation structure than in the personal malice of the criminal.
Most online conversation environments have a structure where personal information—such as phone numbers, external messenger IDs, and profile info—is exposed before sufficient trust is established. Scammers exploit this structure to induce victims to provide information themselves.
The Solution: A Conversation Structure That Doesn't Demand Information

Based on this awareness, the first thing we need to examine is the recurring scam structure in second-hand trading. The problem is not that second-hand trading is inherently dangerous, but rather that personal information is exposed too easily during the process.
The commonly recommended methods to prevent second-hand trade scams are relatively clear: stay within the platform's chat, do not move to external messengers, and do not easily share personal information like phone numbers. Additionally, one should be suspicious of scams if there is a suggestion to bypass secure payment systems.
The problem, however, is that the spaces where scammers operate are not limited to second-hand trading. Environments where anonymous conversation is possible—such as random chat or open chat—are frequently mentioned as areas where scammers can easily approach. In these spaces, conversations quickly become intimate, leading to frequent moves to phone numbers or external contacts. Ultimately, just like second-hand trade scams, info exposure in the early stages of a conversation acts as a primary risk factor.
In this context, conversation environments designed to make the exchange of personal information difficult from the start are being discussed as an alternative for scam prevention.
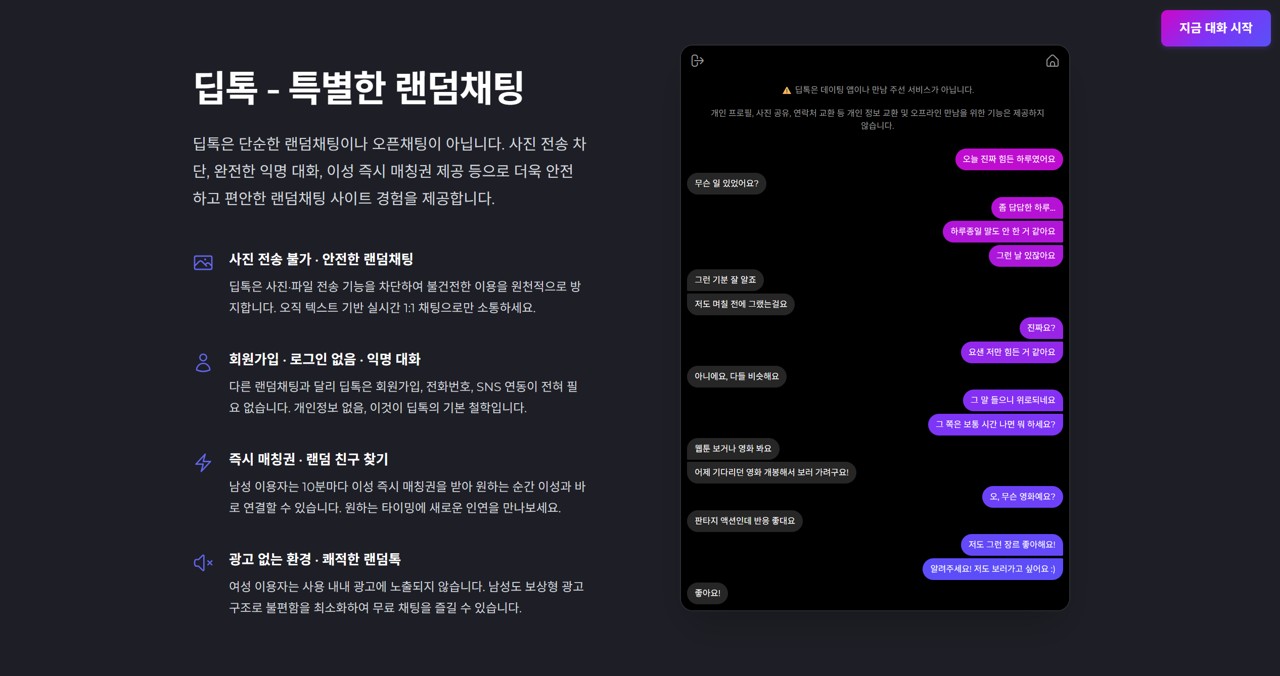
For example, random chat diptok provides a text-based anonymous chat environment that can be used without logging in, does not require exposing a phone number, and leaves no conversation logs. In such a structure, it is difficult for the conditions of a scam to even begin—specifically the method of collecting personal info through conversation and expanding it into secondary damage, as seen in Taxi Driver 3.
This is not a matter of recommending a specific service, but rather an example of which structures create risk and which structures block scams.
Summary
The phone scam episode in Taxi Driver 3 is not an exaggerated dramatic fantasy; it is a case study showing how second-hand trade and online scams expand into crimes that destroy daily life. Ultimately, the key to stopping scams does not lie in figuring out who is a "bad person." Choosing a structure where scams are difficult to operate is a much more realistic response.